IT security and infrastructure
Overview
MainEDC™ is designed to help our Clients work securely with their data and deliver it to users, customers, partners, and investigators to drive better business outcomes. We protect Clients’ data, ensure the following security regulations, and mitigate all potential risks; all of these are essential for building trust and delivering a high-service level. We at Data Management 365 take a risk-based approach to security and technologies implemented to protect our customers.
Our implementation allows us to adhere to the following standards and best practices, demonstrating our commitment to customers’ security and privacy:
- 21 CFR Part 11
- HIPAA
- GDPR
For EAEU regulations:
- State Standard GOST 52379-2005
- State Standard GOST ISO 14155-2014
- Decision N 79 of the Council of the Eurasian Economic Commission “On Approval of the Rules of Good Clinical Practice of the Eurasian Economic Union” dated November 3, 2016.
Please contact our QA Department to obtain more information
Protection Levels
We use only the best scenarios and industry practices to keep and protect customers’ data: from physical security at the data centers to full control using audit trail at data level:
- Processes (SOPs, IQs, PQs, WPs)
- Physical
- Infrastructure
- Virtual environment
- Application
- User
- Data
Processes and procedures
Our strategy revolves around clients’ data security. The key priority for us is well-educated personnel who understand their responsibilities and always keep their knowledge of Company procedures up-to-date.
Data Management 365 QA procedures provide comprehensive guidelines for security processes and policies to ensure the security of our customers’ data. We use validated Electronic Learning Management System (eLMS) to ensure that our employees are familiarized and trained in the applicable standard operation procedures and working instructions.
Please contact our QA Department to obtain more information
21 CFR Part 11
MainEDC™ is compliant with the FDA requirements (Part 11 of Title 21 of Code of Federal Regulations, U.S. Department of Health and Human Services; 21 CFR Part 11), including:
- Safe electronic records storage, quick and accurate retrieval throughout the entire period of their retention
- Automatically generated audit trails which record the time and date of each entry and action performed by any system user
- Credentials verification to ensure that only authorized individuals can use the system in accordance with their access rights
- Operational system checks to enforce permitted sequencing of steps and events in the system
- Password aging and other privacy processes to ensure the highest level of security for your data
- Electronic signature protocols to provide integrity between the record and the signature attached to it
Data Management 365 confirm meeting 21 CFR Part 11 technical requirements by employing necessary operational procedures and controls that include validation of GxP functions to ensure accuracy, reliability, consistent intended performance, and the ability to recognize invalid or altered records.
Please contact our QA Department to obtain more information
GDPR
We provide our customers the tools that allow them to meet their data controller responsibilities under the GDPR. The examples of such tools are:
- tools for data pseudonymization (as required by Article 32 of GDPR)
- strong control of the system access rights
- tool for data download at the sites at the end of the study. As required by Article 28.3 of GDPR: the processor deletes or returns all the personal data to the controller after the end of the provision of services relating to processing.
- all traffic is encrypted using TLS/SSL protocol that leverages either SHA-2 or AES algorithms
- all access to the user interfaces is encrypted via HTTPS/SSL
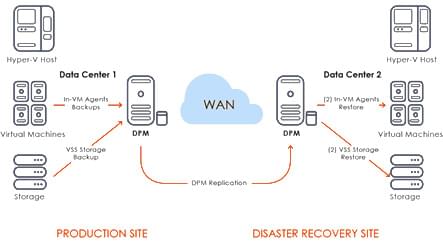
Business Continuity and Disaster Recovery
Ensuring business process continuity and emergency data recovery is an integral part of our company’s systemic approach to work. All functional areas are involved in the business process, including support service, human resources, management functions, and customer application disaster recovery plan.
Please contact our QA Department to obtain more information
Data Centers
One of the most important aspects of our work along with multitasking and flexibility is the reliability of data storage and uninterrupted access to our services. We use the latest fail-safe technology to ensure the accessibility and security of data.
We use only certified data centers:
- Reliable hardware
- Virtualization
- Clusterization
- Data storage on a private cloud for each client
- Monitoring of the systems 24/7
- Reliable reserve backup
- Strict access rules
Our Data Centers
Currently Data Management 365 uses the following data centers:
- Hetzner Online (Falkenstein, Germany)
- Hetzner Online (Nuremberg, Germany)
- Hetzner Finland Oy (Tuusula, Finland)
- Webzilla (Texas, USA)
- IBM Softlayer (Singapore)
- Selectel (Moscow, Russia)
- Verizone UK5 (London, UK)
We are constantly expanding the list of our data centers. Some data centers which is not in the list are used as part of a client-specific agreement.
Virtualization, Replication, and Clusterization
We use Microsoft Hyper-V Server 2016 and the clusterization technology.
Private Cloud Data Storage / Dedicated Server
Each client is provided with their own private cloud hosted on Windows 2016/2019. We do not use common databases, password databases or different access links for different clients within the same site. Each site has its own access level and owns backup copies, thereby reducing the possibility of data leakage between different clients to an absolute zero.
Monitoring
All of our services are under 24/7 monitoring. We use both external services (Selectel) for general alerts (ping, https access etc.) and deep monitoring using Zabbix tool. Any potential infrastructure problems, connection problems, and all the services are constantly surveyed, if the system recognizes a possible problem, the technical support team of the company immediately receives email, SMS alerts and Telegram messages.
Data backup
We are in complete charge of the security of data, which is why we use the best experience in data storage and backup technology.
We use GFS (grandfather-father-son) HDD rotation strategy.
We perform incremental backup two times per day including weekends.
We perform FULL backup every day including weekends.
We keep the last two weeks of data (14 HDD), one HDD for the previous two weeks, one HDD per each month of the year and one HDD per each year all the time.
Each Monday, we deposit an encrypted (2048 key) backup in a bank safe (out of the data center).
Physical Security
All Data Centers used by Data Management 365 have passed the vendor assessment procedure according to strict corporate standards. All of the data centers correspond to the following criteria:
- Have the necessary certification
- Use reliable hardware
- Feature N+1 redundant HVAC and UPS
- Provide a private cloud for each client’s data storage
- Ensure 24/7 systems monitoring
- Guarantee reliable reserve backup
- Have strict access rules (Uniformed Guards, Photo-ID Smart Cards, Video Surveillance)
- Located in nondescript buildings
We are constantly expanding the approved list of our data centers.
Hardware and Internet Channels
We use only reliable servers, produced by Dell, HP, and Supermicro. Standard specification is: 2 x Intel Xeon Silver 4114 2.2 GHz, 20 cores, 128Gb DDR3, 6x 960 GB SSD, Raid 1 + Raid 10, 1000 Mbit/s Internet connection.
Infrastructure
Data Management 365 uses the most reliable solution in terms of both the reliability of storage and the availability of data. As an OS level, we use the time-tested solution from Microsoft – Microsoft Hyper-V Server 2016 to maintain a robust disaster recovery strategy, we use two main technologies – replication and clustering (see Backup Strategy section). We keep all of the internal data and clients’ data only on virtual machines.
Replication
Thanks to the Microsoft Hyper V solution, any Virtual Machine with all of the data is replicated online to another data center.
Clustering
The Failover Clustering feature enables Data Management 365 to create and manage failover clusters. A failover cluster is a group of independent computers that work together to increase the availability of applications and services. The clustered servers are connected by https online replication. If one of the cluster nodes fails, another node begins to provide service. Users experience only minimal disruptions in service.
Segmented/Isolated Client’s Data
Data Management 365 Platform provides each client with their own virtual environment and personal domain to access the application. Therefore, the mixing of data is excluded. This physical security measure is in addition to the logical security measures.
Firewalls
All network access to the hosts is protected by a multi-layered firewall operating in a deny-all mode. Internet access is only permitted on explicitly opened ports for only a subset of specified hosts.
Virus, Spybot, Spam Scanning
In addition to our Firewall, Data Management 365 uses a number of scanning tools for the further sanitization of all data prior to its traversing to the data center networks. These scanning tools notify us if something malicious has made it through our defenses and may attempt to access our systems.
Networking
Data Management 365 servers are allocated to the different security groups with specific security settings. Separate VLANs are used for split testing, QA and production environments.
Data Management 365 Applications
User’s Password
The Data Management 365 applications don’t just provide the end users with the ability to access data, the system controls all of the security parameters of each system’s user according to the client specific model. The architecture relies on a centralized authentication and authorization security framework to control access to services. By default, each user must change the password every 90 days. Passwords are to be complicated and fulfill a number of requirements, including the number and type of symbols.
The system controls a number of access attempts and stops using the last user password after the 3rd selection attempt to reduce the risk of automated attacks against customer data. Our clients may also choose to implement Single-Sign-On (SSO) with their own access policies (including multi-factor access) to integrate user authentication with their own policy (e.g. Active Directory).
Multi-Factor Authorization
Data Management 365 platform supports Multi-Factor Authorization (MFA) using 3rd factor e-mail / text notifications.
User Session Expiration
User session expiration (timeout) allows our clients to specify a period of inactivity after which user sessions are terminated and users are automatically logged out of the Data Management 365 platform. In accordance with industry best practices, we recommend configuring the user session expiration for HIPAA compliance or other security-sensitive solutions. By default, the timeout in the system is 20 minutes, which can be changed according to the client’s specific settings.
Encryption-in-Transit
All traffic into and out of the Data Management 365 Platform is encrypted using TLS/SSL protocol that leverages either SHA-2 or AES algorithms.
Application Access
Whether an end-user is accessing dashboards or reports in the Data Management 365 Platform user interface or an administrator configuring an environment using the configuration tools, all access to the user interfaces is encrypted via HTTPS/SSL.
Integration
Any integration with the Data Management 365 application programmatic interface (API) leverages HTTPS/SSL encryption.
Application Access
Customer data may only be accessed through the application layer. Whether this access is through the user interfaces or through the available API, it enforces user access controls to regulate access to the customer data only to authorized users and Data Management 365 employees. Data Management 365 does not provide direct access to any database.
End User and Roles
User security is enforced via a variety of security measures allowing only authorized users to view a strictly defined set of data based on a user’s role or personal settings. For example, a user with a CRA role will not be able to gain access to financial data, etc.
IP Whitelisting
IP Whitelisting is an additional security feature provided by Data Management 365. This feature should be used to limit and control access based on a list of defined IP addresses or address ranges from which users can access the Data Management 365 Application. We recommend our client to configure IP Whitelisting for HIPAA compliant solutions in accordance with industry best practices.
Audit Trail
Audit trails maintain a record of system activity both by system and application processes and by the user activity of systems and applications. In conjunction with the appropriate tools and procedures, audit trails can assist in detecting security violations, performance problems, and flaws in applications. Using an application audit trail, we always can restore any events in the system. We use an audit trail for all activities (including login/logout, insert, update and delete operations) that always remain for the whole application lifecycle as a read-only source. Any record in the audit trail includes the name of the user and timestamp in international format.
Periodic Vulnerability Testing
Data Management 365 has the third-party annual vulnerability and penetration testing which covers Top Application Security Flaws.
We are proud that our customers’ data is sufficiently protected by this approach and we are open to discussing any practices and approaches further.
Membership
Data Management 365 is a member of the Microsoft BizSpark ® program. As a participant in this program, Data Management 365 gains access to software development tools, platform technologies and server products, support and training from Microsoft.
